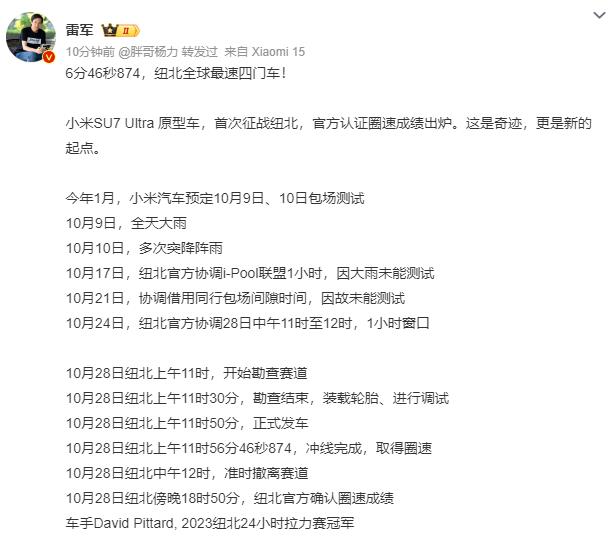
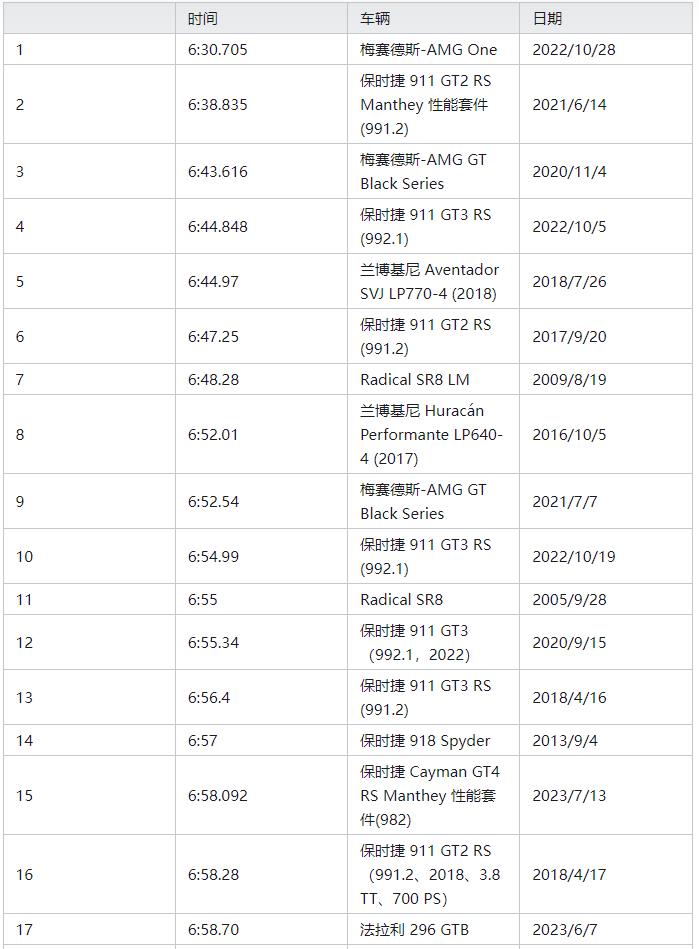
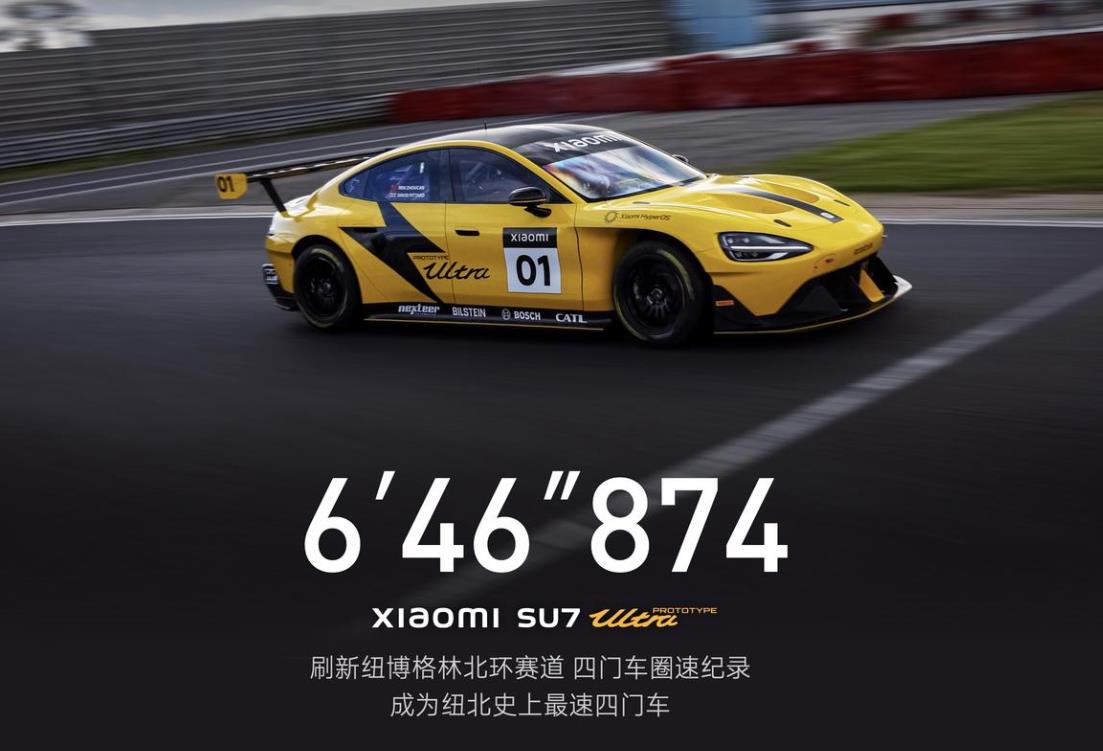
Recently, the new flagship model AITO Wenjie M9 of Sailis Automobile was officially released. After AITO Wenjie M7, it injected explosive extended-range models into the new energy automobile market. AITO asked M9 to release more than 10,000 reservations in two hours.

Wen Jie M9 Source: AITO official websiteCoincidentally, Chen Zhuo, president of Aouita Science and Technology, recently announced the new car plan for 2024, saying that Aouita will launch brand-new extended-range products in 2024. Subsequently, Aouita officials further indicated that four extended-range power models will be launched.
Previously, it was reported in the industry that Xiaomi was also laying out extended-range vehicles, and Xiaomi official website also released the position of design and development engineer for extended-range systems.
In recent years, China’s hybrid passenger car market has experienced explosive growth, especially extended-range vehicles, which have played an important role in promoting China’s electrification transformation.
As early as the 12th China Automobile Forum at the end of 2022, Zhang Yongwei, Vice Chairman and Secretary General of committee of 100, China Electric Vehicle, publicly stated that the extended-range route is a unique route in China, which originated from the market, is a technical route driven by consumer demand, and has quickly become an effective supplement to pure circuit lines in the development process, and its future development is worthy of market attention.
For this reason, China Electric Vehicle committee of 100 and Chebai Think Tank launched the research report "The Development Prospect of Hybrid Passenger Cars II: The Development Prospect of Hybrid Passenger Cars in China" (hereinafter referred to as committee of 100 Research Report), which made an in-depth study on the development of hybrid vehicles including extended-range vehicles.

Committee of 100 Research Report Home PageCommittee of 100 research report shows that in China, hybrid vehicles including extended-range vehicles have achieved explosive growth, but they will also encounter bottlenecks in development.
According to the committee of 100 Research Report, extended-range vehicles are the first choice for the new forces to lay out the hybrid market.
In October 2018, LI released the extended-range SUV Li ONE, and the market began to pay attention to extended-range technology. The extended-range vehicle is closer to pure electricity. Compared with plug-in and hybrid electric vehicles, the extended-range vehicle uses a larger battery, which is completely driven by a motor and can be externally charged. When the power is insufficient, the fuel engine is used to generate electricity to extend the cruising range.
Since 2021, many car companies have flooded into the extended track. Cyrus and Huawei cooperated to launch the extended-range vehicle boundary series; Dongfeng Lantu, Chang ‘an Deep Blue, Zero Run, Nezha and other brands also laid out pure electricity and extended range routes.
Extended range vehicles are increasingly recognized by consumers. From January to October, 2023, the sales volume of extended-range vehicles has exceeded 400,000, among which the monthly sales volume of ideal brands has continuously exceeded 30,000, and the market share of SUVs above 300,000 is higher than that of luxury brands such as Mercedes-Benz and BMW Audi.
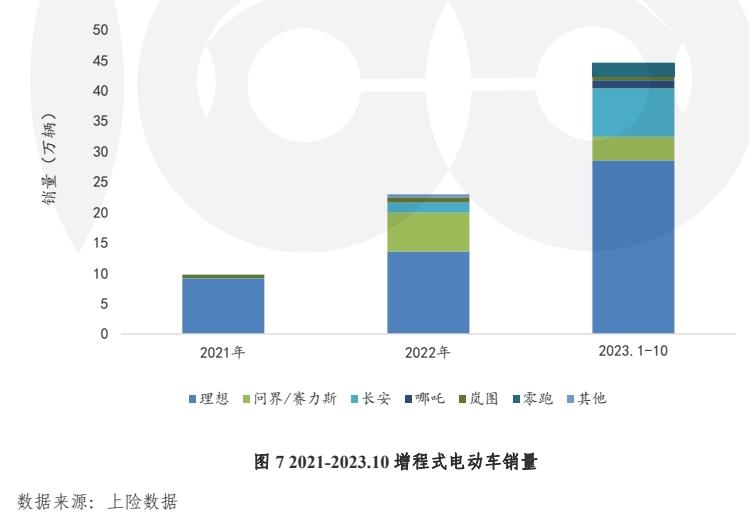
At present, the ideal of success in extended-range vehicles, as well as the executives of Huawei BU, greatly praised extended-range vehicles, and contradicted the once popular statement that "extended-range vehicles are backward technology".
For example, Li Xiang, CEO of LI, thinks that saying that extended-range electric is an backward technology is "nonsense" of a group of technicians who have no user thinking and don’t care about users at all. Yu Chengdong of Huawei BU believes that an extended-range vehicle "is actually a pure electric vehicle if the extended-range engine is removed". The news from the "Seminar on Development Prospects of Hybrid Passenger Cars" held in committee of 100 shows that the industry has accepted the technical route of extended range vehicles, and the market for extended range vehicles is becoming mature.
In 2022, Yu Chengdong also said that extended range is the most suitable new energy vehicle mode at present.
Regarding the positioning and future of the extended program technical route, Zhang Yongwei, vice chairman and secretary general of China Electric Vehicle committee of 100, said that the future development of the extended program technical route is worthy of market attention, and predicted that in the next 10-20 years, the extended program and the hybrid technology route still have a good development space.
In October, 2023, seven departments jointly issued the Work Plan for Steady Growth of Automobile Industry in 2023-2024, which clearly stated that it was necessary to "encourage the development of hybrid power and low-carbon fuel technologies".
The emergence of extended-range vehicles actually stems from the precise control of the user experience by new car companies.
When the new forces started their business, the mileage anxiety of electric vehicles was very serious, and the extended-range vehicle was equipped with an extended-range engine on the basis of electric vehicles, which can achieve "daily electricity consumption, no electricity and no oil", which is an important choice to alleviate mileage anxiety. As an early extended-range car, Li ONE’s slogan is "Electric car without mileage anxiety".
Although the extended-range car has no mileage anxiety, after entering the power loss state, the fuel consumption increases linearly, and some owners of extended-range cars frequently complain that the fuel consumption is high at high speed. The main reason is that the engine can’t directly drive the vehicle under the extended-range series structure, so the gasoline needs to be converted into mechanical energy in the engine first, and then the mechanical energy is converted into electrical energy through the generator, and the electrical energy is finally converted into mechanical energy by the driving motor. After many energy conversions, the loss will naturally be "folded up".
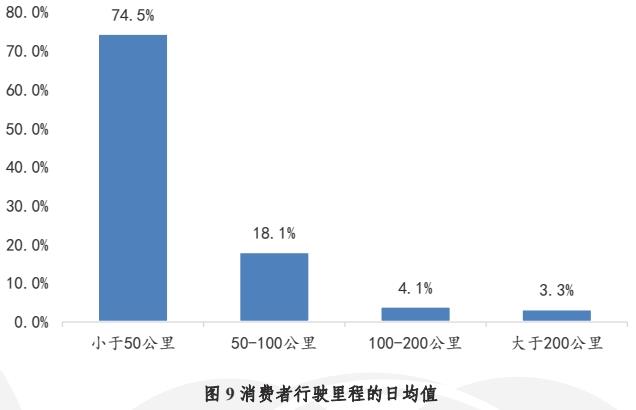
However, this shortcoming is not the focus of attention for car buyers. At present, users who buy cars have more driving environments in urban areas and rarely travel long distances. Committee of 100 Research Report shows that consumers buy cars mainly for daily commuting, and the average daily mileage of 74% respondents is less than 50 kilometers, so most users of extended-range cars rarely experience the disadvantage of high fuel consumption.
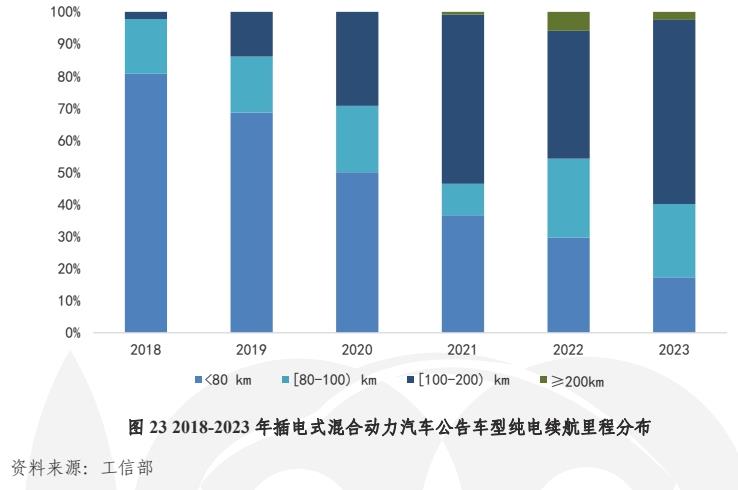
Moreover, the new car announcement data of the Ministry of Industry and Information Technology shows that in recent years, the pure electric cruising range of plug-in hybrid vehicles, including extended range, has been continuously improved, and it has gathered in the range of 100-200 kilometers.
The most important thing is that for the majority of users, the extended-range car is more economical.
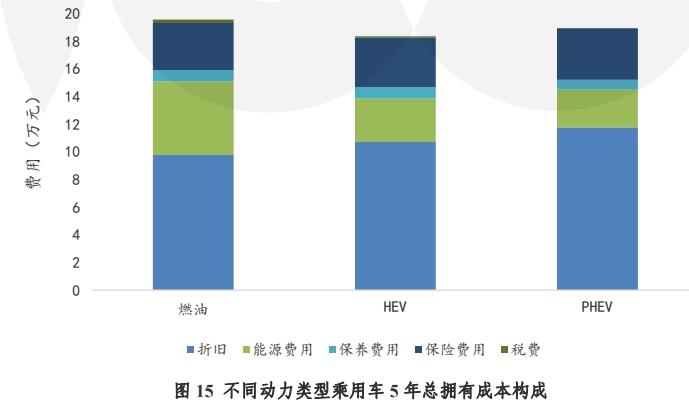
According to the research report of committee of 100, the total cost of hybrid electric vehicles is about 4,000 yuan lower than that of fuel vehicles, and the total cost of hybrid electric vehicles (including extended-range vehicles) can be saved about 10,000 yuan under the assumption that the average annual mileage is 15,300 kilometers during the five-year use.
In addition to meeting the needs of consumers, extended-range vehicles are also good for car companies, mainly reflected in the low cost.
According to the committee of 100 Research Report, new energy passenger car enterprises are facing greater operating pressure due to multiple factors such as insufficient supply of spare parts, fluctuation of raw material prices and price war, and the hybrid route including extended range can help enterprises to alleviate the operating pressure. In the first half of 2023, five new energy listed car companies with pure electricity suffered losses. However, hybrid electric vehicles have a certain cost advantage over pure electricity. For example, the BOM cost of a large SUV in a plug-in hybrid vehicle is about 20% lower than that of pure electricity of the same level. Therefore, the hybrid route can help enterprises reduce costs and open up sales.
Moreover, hybrid power, including extended range, can continue to promote the innovation and development of the three power technologies. A number of domestic independent engine enterprises have taken advantage of the east wind of extended-range vehicles to glow with new vitality. For example, in 2019, Harbin dongan power provided range extenders for Li ONE, and in 2020, its engine business revenue increased by 70% year-on-year. Later, dongan power cooperated with Tianji, Nezha, Zero Run and other enterprises to further expand the market.
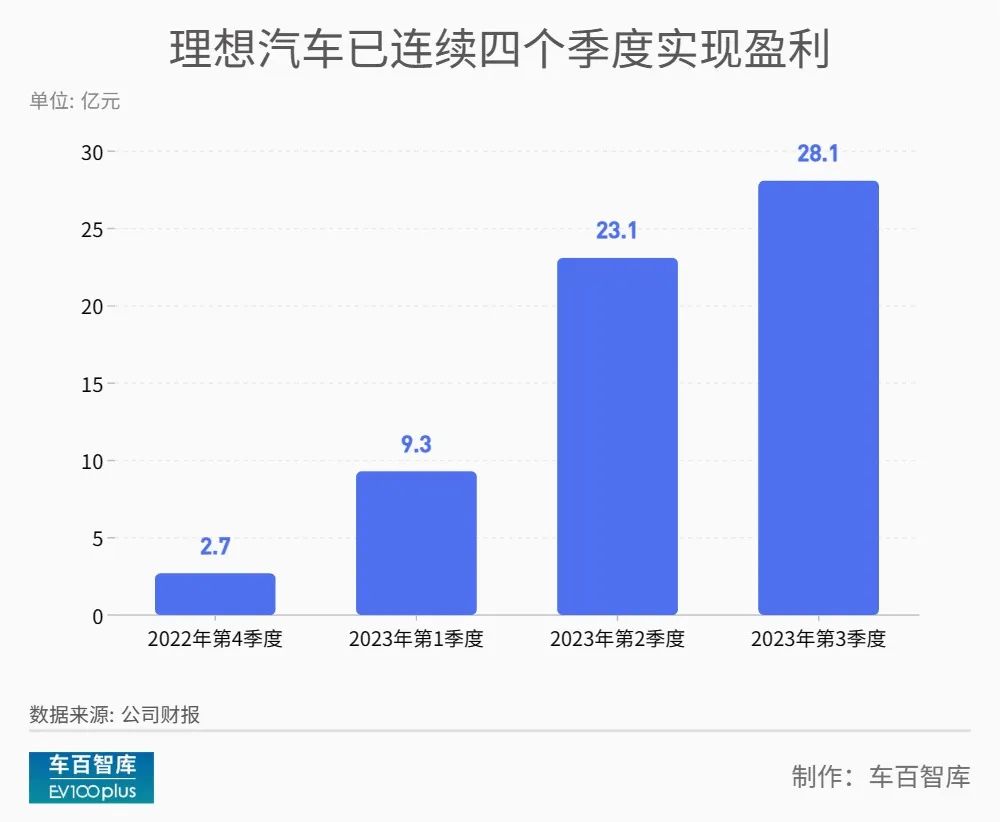
Compared with other new power car companies that take the pure circuit line, LI can make a profit for four consecutive quarters, which has nothing to do with its insistence on the technical route of extended-range cars.
Compared with fuel vehicles, hybrid vehicles such as extended-range vehicles are also easier to combine with intelligence.
This is because the battery of traditional fuel vehicles is small, and it is difficult to meet the demand of intelligence. The power battery of hybrid vehicles such as extended-range vehicles provides power guarantee for intelligent equipment. Therefore, hybrid technology will be deeply integrated with intelligent driving and intelligent cockpit technology.
A well-known example is the deep cooperation between Cyrus and Huawei, which makes the series of extended-range vehicles equipped with intelligent cockpit system and Huawei advanced intelligent driving system on the basis of electrification, bringing a leading intelligent experience.
However, this does not mean that the development of extended-range vehicles will be smooth sailing, on the contrary, its development will also encounter a series of bottlenecks.
According to committee of 100 Research Report, the hedging rate has a great influence on the total cost of ownership of plug-in hybrid vehicles, including extended range. It is estimated that after five years, the preservation rate of hybrid electric vehicles is about 50%, while that of plug-in hybrid vehicles including extended range is about 40% due to the attenuation of power batteries. In the future, with the upgrading of battery technology, the value-keeping rate of plug-in hybrids including extended-range vehicles will be improved rapidly.
The adjustment of purchase tax preferential policies will also have a certain impact on plug-in hybrid vehicles including extended-range vehicles. According to the "Announcement on Continuing and Optimizing the Vehicle Purchase Tax Reduction and Exemption Policy for New Energy Vehicles", plug-in hybrid vehicles will be exempted from purchase tax before 2026, and will be halved from 2026 to 2027. When the plug-in hybrid vehicle no longer enjoys the purchase tax, its total cost of ownership advantage will be reduced, and consumers’ willingness to buy plug-in hybrid vehicles will be reduced. According to the survey data in committee of 100 Research Report, about 40% of potential users of plug-in hybrid vehicles, including extended range, may give up buying because of the cancellation of preferential purchase tax policies.
Looking ahead, committee of 100 Research Report shows that hybrid vehicles, especially plug-in hybrid vehicles including extended range, will accelerate the replacement of fuel vehicles.
From the demand side, 36% of consumers intend to choose hybrid vehicles. The excellent power performance and economic performance of hybrid vehicles meet the needs of consumers, and at the same time, they also dispel consumers’ anxiety about cruising range and recharge. From the supply side, the dual-point policy has improved the enthusiasm of car companies to produce hybrid vehicles, and the strength of hybrid products of domestic brands has been continuously improved, and the supply of models has been continuously enriched.
In short, thanks to cost control and economies of scale, the price of hybrid electric vehicles, including plug-in, will further drop, and the market space will continue to expand. In the coming 5-10 years, hybrid vehicles will still have a rapid development momentum, and traditional fuel vehicles will be replaced by hybrid vehicles and pure electricity. It is estimated that the market share of plug-in hybrid vehicles including extended range may reach 30% from 2025 to 2030.
For more detailed research data, opinions and authoritative predictions about hybrid vehicles such as extended range, please refer to committee of 100 Research Report.Topic 2: Development Prospects of Hybrid Passenger Cars in ChinaAnd other related research reports.